CATEGORIES
Activities CentinelBox
Clients & Projects CentinelBox
Products & Services SAP
Products & Services CentinelBox
Tips CentinelBox
Request a FREE demonstration
We are CentinelBox, the best solution to manage the security of your SAP ERP system.
CentinelBox: Your ally in the challenge of external auditors and critical risk control
June 6, 2023
We know that the annual visit from external auditors can be a real challenge for any organization. Wanna turn it into a smooth and successful experience? If you’ve got CentinelBox, you’ve got the solution right at your fingertips. Our innovative risk management system provides you with the necessary tools to tackle the challenges of audits and avoid unnecessary headaches.
The key question is: Were last year’s recommendations fulfilled? To find the answer, it’s essential to meticulously analyze each observation made by the auditors, assess the management’s commitment, and verify the compliance with each recommendation.
And that’s where CentinelBox makes a difference. Our comprehensive and customized reports give you a clear and concise overview of the critical points you need to address.
Allocation and usage of critical profiles? High-criticality transactions? Conflicting SOD transactions? Allocation of critical authorization objects?
With CentinelBox, you’ll have the required reports at your disposal to efficiently control and mitigate these risks. Don’t let external audits catch you off guard.
Here are the CentinelBox reports that support risk control in these areas:
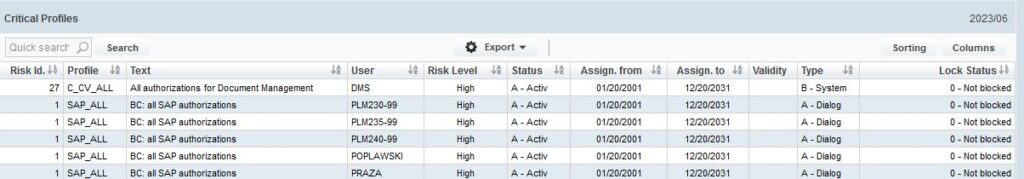
1. Allocation and usage of critical profiles: Based on a definition of 32 standard critical profiles in SAP, we detect their assignment to user accounts:
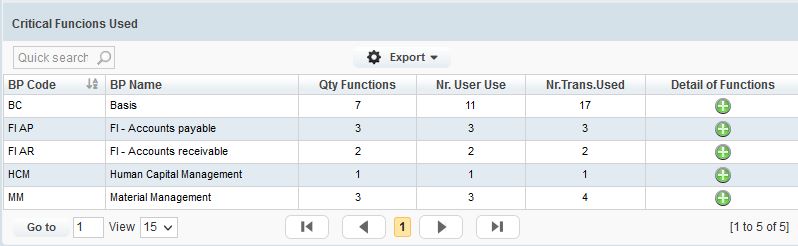
2. Allocation and usage of high-criticality transactions: Based on the definition of critical transactions in the risk matrix, we detect the assignment and usage of these transactions:
3. When navigating into the detailed usage of functions:
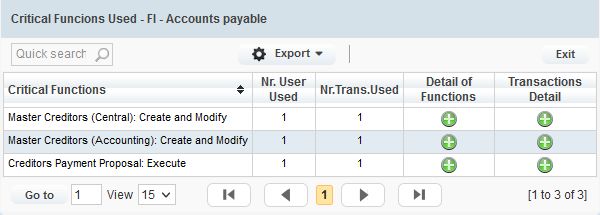
And then it is possible to identify the user accounts that have used them.
4. Allocation and usage of conflicting SOD transactions: Based on the definition of conflicting transactions in the risk matrix, we detect the assignment and usage of these transactions:
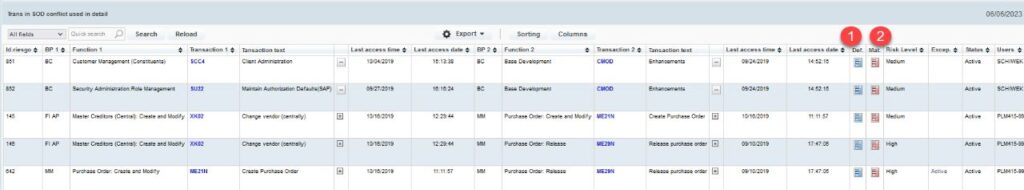
The definition of the objects that determine the risk is obtained by selecting (1), and their materialization is done in (2).
5. Allocation of critical authorization objects: Based on the definition in the risk matrix, we detect their assignment:
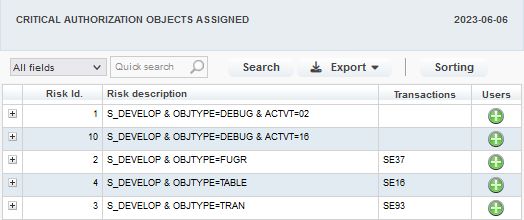
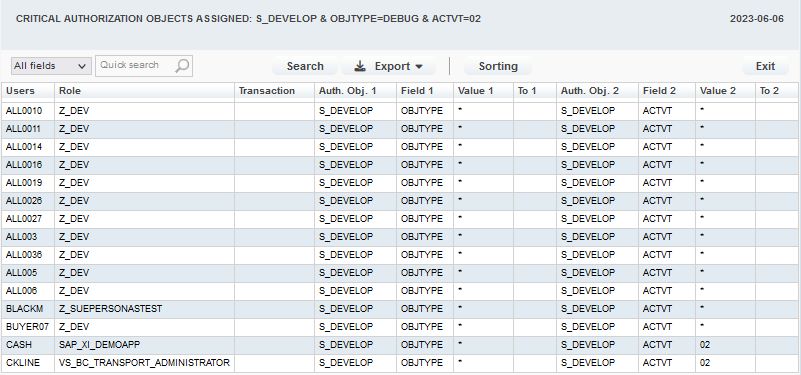
6. And the detailed overview of user accounts:
Want to learn more about CentinelBox and how we can help you take control of your SAP Security?
Schedule a personalised demo directly with me so you can see how our platform enables assertive and successful internal control.
Leave a Reply Cancel reply
Australia
Luo & Mont'YA IT Services
72 Woodlands Drive, Rochedale South, 4123
+61 403 286 968
Contact: Hernan Montoya
© 2024 CentinelBox. All rights reserved
Chile
TwoBox Ing. De Sistemas
contact@centinelbox.com
(569) 3202 7181
Perú
ATIQ Consultoría
www.atiqconsultoria.com
Info@atiqconsultoria.com
+51 932 266 090
México
www.centinelbox.mx
contact@centinelbox.mx
+52 1 55 1798 5870